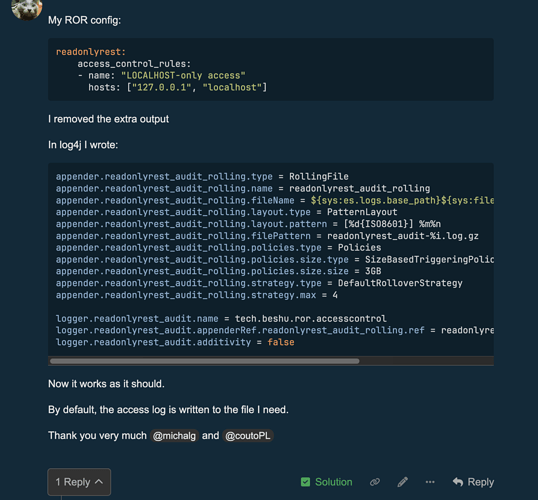
I noticed, that you are not currently using the log4j2.properties file, that I provided earlier. I’ve just tested it using the config that you have provided and I experience the same issues. But when I switched to the log4j2 file that I posted earlier it works fine.
So you can either use the log4j2 file that I provided earlier. Or second option - you can fix 3 lines in your current log4j2.properties file.
Those 3 lines need to be removed: (line 1 and 3 look the same, but in your config they end with spaces, which is not allowed, in line 2 the appender ref was incorrect):
logger.readonlyrest_audit.name = readonlyrest_audit
logger.readonlyrest_audit.appenderRef.ror_audit.ref = readonlyrest_audit_rolling
logger.readonlyrest_audit.additivity = false
And they need to be replaced with:
logger.readonlyrest_audit.name = readonlyrest_audit
logger.readonlyrest_audit.appenderRef.readonlyrest_audit_rolling.ref = readonlyrest_audit_rolling
logger.readonlyrest_audit.additivity = false