Hi Simone,
We’ve finished Proof of concept testing this in our local and everything worked perfectly. we deployed these changes to our AWS EC2 Instances (only the Kibana and Elastic). For testing NGINX config, we are trying to talk to the Remote EC2 Kibana instance from our Local NGINX (as opposed to what we tried above successfully - local NGINX to local KIBANA to local Elastic).
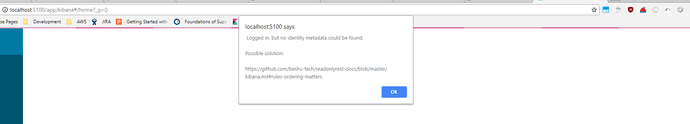
What happens is when we try to point local NGINX (ie call http://localhost:5100 NGINX endpoint) to the remote Kibana above, we’re not seeing any hits on ElasticSearch. Instead, we get a popup that states “Logged In, but no identity metadata could be found”. Also, running developer tools, I see this weird error in the network tab of developer console:
INFO: 2018-06-26T19:21:33Z
Adding connection to http://localhost:5100/elasticsearch vendors.bundle: 165
no username found in identity, logging out {authHeaders: {…}, hiddenApps: Array(0), sid: "a3b90eba-c5ac-4ce0-8a69-20babcf83050"} commons.bundle: 3
NGINX Conf:
http {
include mime.types;
default_type application/octet-stream;
log_format main '$remote_addr - $remote_user [$time_local] “$request” ’
sendfile on;
keepalive_timeout 65;server {
listen 5100;
server_name localhost;location / { rewrite ^/(.*) /$1 break; proxy_ignore_client_abort on; proxy_pass https://myapp-kibana.myhost.com; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $http_host; proxy_set_header x-forwarded-user ADM123; proxy_set_header x-forwarded-group admin; }}
}