Hi there,
We are using ES 6.5.0 with readonlyrest-1.20.0_es. (also tested in DEV with newest version readonlyrest-1.22.1_es6.5.0 and issue still there)
With the configuration listed below, we are facing quite serious security issue in PROD, when data are available across applications using /_search/template API and with SSO shouldn’t be accessible.
_search API is with single-sign-on blocked with 401 with same user and settings (which is expected)
Steps to reproduce:
RoR configuration (in puppet):
readonlyrest:
ldaps:
all:
no_backend: true
groups: "[\"CHR-GP-SV-INL-P-Elasticservice-Prod\"]"
indexes: "[\"*\"]"
actions: "[\"*\"]"
dna:
no_ldap: true
no_backend: true
groups: "[\"CHR-GP-SV-INL-P-ElasticserviceDna-Prod\", \"CHR-GP-SV-DNA-P-USER-Prod\", \"CHR-GP-SV-DNA-P-ADMIN-Prod\", \"CHR-GP-SV-DNA-P-OVERALL-Prod\"]"
indexes: "[\"dna_*\"]"
actions: "[\"indices:data/read/*\", \"cluster:monitor/state\", \"indices:admin/get\", \"indices:admin/mappings/fields/get\", \"indices:admin/mappings/get\", \"indices:admin/aliases/get\", \"indices:admin/template/get\"]"
readonlyrest.yml
readonlyrest:
access_control_rules:
- name: "LDAP - all - Kibana"
type: allow
ldap_auth:
name: "ldap1"
groups: ["CHR-GP-SV-INL-D-Elasticservice-Dev"]
indices: [".kibana*"]
actions: ["indices:data/read/*","indices:data/write/*"]
- name: "LDAP - all"
type: allow
ldap_auth:
name: "ldap1"
groups: ["CHR-GP-SV-INL-D-Elasticservice-Dev"]
indices: ["*"]
actions: ["*"]
- name: "Proxy - all - Kibana"
type: allow
headers: ["X-Auth-Key:..."]
proxy_auth:
proxy_auth_config: "proxy1"
users: ["*"]
ldap_authorization:
name: "ldap1"
groups: ["CHR-GP-SV-INL-D-Elasticservice-Dev"]
indices: [".kibana*"]
actions: ["indices:data/read/*","indices:data/write/*"]
- name: "Proxy - all"
type: allow
headers: ["X-Auth-Key:..."]
proxy_auth:
proxy_auth_config: "proxy1"
users: ["*"]
ldap_authorization:
name: "ldap1"
groups: ["CHR-GP-SV-INL-D-Elasticservice-Dev"]
indices: ["*"]
actions: ["*"]
- name: "Proxy - dna - Kibana"
type: allow
headers: ["X-Auth-Key:..."]
proxy_auth:
proxy_auth_config: "proxy1"
users: ["*"]
ldap_authorization:
name: "ldap1"
groups: ["CHR-GP-SV-INL-D-ElasticserviceDna-Dev", "CHR-GP-SV-DNA-P-USER-Dev", "CHR-GP-SV-DNA-P-ADMIN-Dev"]
indices: [".kibana*"]
actions: ["indices:data/read/*","indices:data/write/*"]
- name: "Proxy - dna"
type: allow
headers: ["X-Auth-Key:..."]
proxy_auth:
proxy_auth_config: "proxy1"
users: ["*"]
ldap_authorization:
name: "ldap1"
groups: ["CHR-GP-SV-INL-D-ElasticserviceDna-Dev", "CHR-GP-SV-DNA-P-USER-Dev", "CHR-GP-SV-DNA-P-ADMIN-Dev"]
indices: ["dna_*"]
actions: ["indices:data/read/*", "cluster:monitor/state", "indices:admin/get", "indices:admin/mappings/fields/get", "indices:admin/mappings/get", "indices:admin/aliases/get", "indices:admin/template/get"]
proxy_auth_configs:
- name: proxy1
user_id_header: "X-Forwarded-User"
ldaps:
- name: ldap1
host: "...."
port: ....
ssl_enabled: true
ssl_trust_all_certs: true
bind_dn: "CN=tecinld1,OU=TEC,OU=SpecialUser,DC=corp,DC=gwpnet,DC=com"
bind_password: "...."
search_user_base_DN: "DC=corp,DC=gwpnet,DC=com"
user_id_attribute: "samaccountname"
search_groups_base_DN: "DC=corp,DC=gwpnet,DC=com"
unique_member_attribute: "member"
connection_pool_size: 10
connection_timeout_in_sec: 10
request_timeout_in_sec: 10
cache_ttl_in_sec: 60
group_search_filter: "(objectClass=group)"
group_name_attribute: "cn"
I’m NOT part of any mentioned group:
- CHR-GP-SV-INL-P-Elasticservice-Prod
- CHR-GP-SV-INL-P-ElasticserviceDna-Prod
- CHR-GP-SV-DNA-P-ADMIN-Prod
- CHR-GP-SV-DNA-P-OVERALL-Prod - this has 5000+ participants
- CHR-GP-SV-DNA-P-USER-Prod - this group is no longer available (not existing)
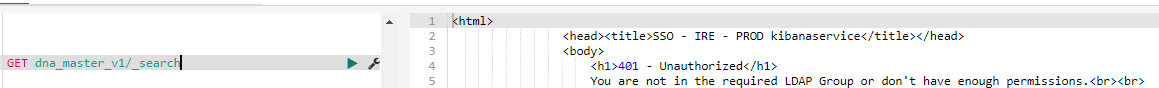
In that configuration _search API returns 401 (which is expected)
GET dna_master_v1/_search
but _search/template against dna_* index returns data I should not see
GET dna_master_v1/_search/template
{
"id":"dna_filter_v1",
"params": {
"search_string":"*"
}
}
{
"took" : 5131,
"timed_out" : false,
"_shards" : {
"total" : 3,
"successful" : 3,
"skipped" : 0,
"failed" : 0
},
"hits" : {
"total" : 704833,
"max_score" : 1.0,
"hits" : [
{
"_index" : "dna_master_v1",
"_type" : "default",
"_id" : "2881",
"_score" : 1.0,
"_source" : {
"summary" : "Kick off conf ...
Can you please help us understanding, what is wrong there?
It looks, that this is related to RoR only.
In the log, access to all indices is logged (IDX:*)
[INFO ][t.b.r.a.l.AccessControlLoggingDecorator] [elasticservice-client-03] e[36mALLOWED by { name: 'Proxy - dowjones - Kibana', policy: ALLOW, rules: [proxy_auth,ldap_authorization,headers_and,actions,indices] req={ ID:30181286-653783344#4501833, TYP:SearchTemplateRequest, CGR:N/A, USR:s48qaf, BRS:false, KDX:null, ACT:indices:data/read/search/template, OA:10.62.28.9/32, XFF:x-forwarded-for=10.92.58.220, DA:10.92.58.228/32, IDX:*, MET:POST, PTH:/dna_master_v1/_search/template, CNT:<OMITTED, LENGTH=70.0 B> , HDR:Authorization=<OMITTED>, Connection=close
Thank you for your quick response in advance.
Dominik