I am trying to setup a POC setup with Kibana / ELS on same node along with authentication supported by ROR
We have successfully setup 3 ELS / 1 kibana setup earlier and had no issues. I need some advice on the above mentioned single node setup as it doesn’t seem to like the authentication attempts currently
I believe the ROR was successfully loaded
[2021-12-18T09:51:34,619][INFO ][t.b.r.b.RorInstance ] [HOSTNAME] ReadonlyREST core was loaded ...
[2021-12-18T09:52:14,553][DEBUG][t.b.r.a.b.Block ] [HOSTNAME] [::KIBANA-SRV::] the request matches no rules in this block: { ID:613347383-1611495040#341, TYP:GetRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:indices:data/read/get, OA:127.0.0.1/32, XFF:null, DA:127.0.0.1/32, IDX:.kibana, MET:GET, PTH:/.kibana/_doc/space:default, CNT:<N/A>, HDR:Connection=keep-alive, Host=localhost:9200, content-length=0, user-agent=elasticsearch-js/7.10.0-rc.1 (linux 3.10.0-693.el7.x86_64-x64; Node.js v10.23.1), x-elastic-product-origin=kibana, x-opaque-id=6b8aa020-d1fa-4690-a48b-47b268a48219, HIS:[::KIBANA-SRV::-> RULES:[auth_key->false] RESOLVED:[indices=.kibana]], }
[2021-12-18T09:52:14,554][DEBUG][t.b.r.a.b.Block ] [HOSTNAME] [::ELS::] the request matches no rules in this block: { ID:613347383-1611495040#341, TYP:GetRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:indices:data/read/get, OA:127.0.0.1/32, XFF:null, DA:127.0.0.1/32, IDX:.kibana, MET:GET, PTH:/.kibana/_doc/space:default, CNT:<N/A>, HDR:Connection=keep-alive, Host=localhost:9200, content-length=0, user-agent=elasticsearch-js/7.10.0-rc.1 (linux 3.10.0-693.el7.x86_64-x64; Node.js v10.23.1), x-elastic-product-origin=kibana, x-opaque-id=6b8aa020-d1fa-4690-a48b-47b268a48219, HIS:[::ELS::-> RULES:[auth_key->false] RESOLVED:[indices=.kibana]], }
Readonly rest file
access_control_rules:
- name: "::KIBANA-SRV::"
auth_key: kibana:somepass
verbosity: info
- name: "::ELS::"
hosts: ["127.0.0.1"]
auth_key: elastic:somepass
verbosity: info
It will result in the below error when i try to access kibana UI
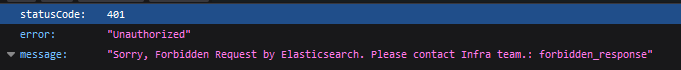
I see the below entry which i am concerned about
USR:[no info about user]
Why will no user be passed on the request and is this the reason its not hitting any blocks and ending in 401 ?