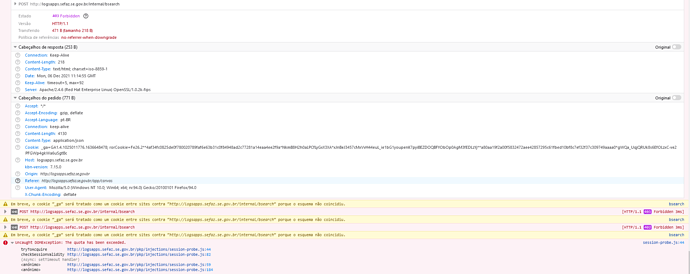
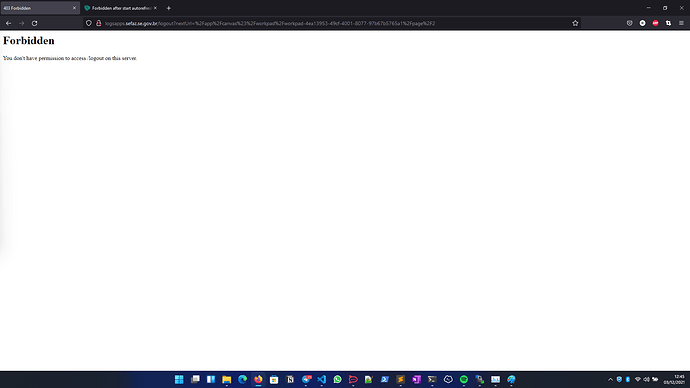
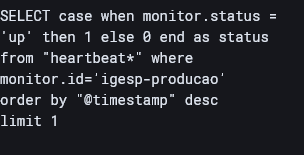
Hi, i’ll send my logs:
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:21:34,394Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:1410496141-1529426443#3161917, TYP:MainRequest, CGR:N/A, USR:elastic (attempted), BRS:true, KDX:null, ACT:cluster:monitor/main, OA:172.29.0.6/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/, CNT:<N/A>, HDR:Accept-Encoding=gzip, Accept=application/json, Authorization=<OMITTED>, Host=elasticsearch:9200, User-Agent=Go-http-client/1.1, content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:22:04,397Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:1608643633-50166409#3163074, TYP:MainRequest, CGR:N/A, USR:elastic (attempted), BRS:true, KDX:null, ACT:cluster:monitor/main, OA:172.29.0.6/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/, CNT:<N/A>, HDR:Accept-Encoding=gzip, Accept=application/json, Authorization=<OMITTED>, Host=elasticsearch:9200, User-Agent=Go-http-client/1.1, content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:22:23,087Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:1571602092-2015646397#3163730, TYP:RRUserMetadataRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:cluster:ror/user_metadata/get, OA:172.29.0.3/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/_readonlyrest/metadata/current_user, CNT:<N/A>, HDR:Accept-Encoding=gzip,deflate, Accept=*/*, Connection=close, Host=elasticsearch:9200, User-Agent=node-fetch/1.0 (+https://github.com/bitinn/node-fetch), content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:22:31,871Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:1996530766-1728309856#3163982, TYP:RRUserMetadataRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:cluster:ror/user_metadata/get, OA:172.29.0.3/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/_readonlyrest/metadata/current_user, CNT:<N/A>, HDR:Accept-Encoding=gzip,deflate, Accept=*/*, Connection=close, Host=elasticsearch:9200, User-Agent=node-fetch/1.0 (+https://github.com/bitinn/node-fetch), content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:22:34,401Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:2094434365-394421213#3164042, TYP:MainRequest, CGR:N/A, USR:elastic (attempted), BRS:true, KDX:null, ACT:cluster:monitor/main, OA:172.29.0.6/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/, CNT:<N/A>, HDR:Accept-Encoding=gzip, Accept=application/json, Authorization=<OMITTED>, Host=elasticsearch:9200, User-Agent=Go-http-client/1.1, content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:22:39,429Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:1116741251-226747544#3164227, TYP:RRUserMetadataRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:cluster:ror/user_metadata/get, OA:172.29.0.3/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/_readonlyrest/metadata/current_user, CNT:<N/A>, HDR:Accept-Encoding=gzip,deflate, Accept=*/*, Connection=close, Host=elasticsearch:9200, User-Agent=node-fetch/1.0 (+https://github.com/bitinn/node-fetch), content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:22:53,114Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:1778568975-1306264829#3164549, TYP:RRUserMetadataRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:cluster:ror/user_metadata/get, OA:172.29.0.3/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/_readonlyrest/metadata/current_user, CNT:<N/A>, HDR:Accept-Encoding=gzip,deflate, Accept=*/*, Connection=close, Host=elasticsearch:9200, User-Agent=node-fetch/1.0 (+https://github.com/bitinn/node-fetch), content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:23:03,676Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:2005900520-776179147#3165141, TYP:RRUserMetadataRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:cluster:ror/user_metadata/get, OA:172.29.0.3/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/_readonlyrest/metadata/current_user, CNT:<N/A>, HDR:Accept-Encoding=gzip,deflate, Accept=*/*, Connection=close, Host=elasticsearch:9200, User-Agent=node-fetch/1.0 (+https://github.com/bitinn/node-fetch), content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:23:04,404Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:503435632-868824448#3165157, TYP:MainRequest, CGR:N/A, USR:elastic (attempted), BRS:true, KDX:null, ACT:cluster:monitor/main, OA:172.29.0.6/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/, CNT:<N/A>, HDR:Accept-Encoding=gzip, Accept=application/json, Authorization=<OMITTED>, Host=elasticsearch:9200, User-Agent=Go-http-client/1.1, content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:23:34,408Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:79689881-1422589300#3166118, TYP:MainRequest, CGR:N/A, USR:elastic (attempted), BRS:true, KDX:null, ACT:cluster:monitor/main, OA:172.29.0.6/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/, CNT:<N/A>, HDR:Accept-Encoding=gzip, Accept=application/json, Authorization=<OMITTED>, Host=elasticsearch:9200, User-Agent=Go-http-client/1.1, content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:23:48,156Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:1218597125-1312867719#3166589, TYP:RRUserMetadataRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:cluster:ror/user_metadata/get, OA:172.29.0.3/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/_readonlyrest/metadata/current_user, CNT:<N/A>, HDR:Accept-Encoding=gzip,deflate, Accept=*/*, Connection=close, Host=elasticsearch:9200, User-Agent=node-fetch/1.0 (+https://github.com/bitinn/node-fetch), content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:23:57,518Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:733530069-77177151#3167049, TYP:RRUserMetadataRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:cluster:ror/user_metadata/get, OA:172.29.0.3/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/_readonlyrest/metadata/current_user, CNT:<N/A>, HDR:Accept-Encoding=gzip,deflate, Accept=*/*, Connection=close, Host=elasticsearch:9200, User-Agent=node-fetch/1.0 (+https://github.com/bitinn/node-fetch), content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:24:04,412Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:1726862675-1972000379#3167272, TYP:MainRequest, CGR:N/A, USR:elastic (attempted), BRS:true, KDX:null, ACT:cluster:monitor/main, OA:172.29.0.6/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/, CNT:<N/A>, HDR:Accept-Encoding=gzip, Accept=application/json, Authorization=<OMITTED>, Host=elasticsearch:9200, User-Agent=Go-http-client/1.1, content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:24:34,416Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:1496038545-242955340#3168220, TYP:MainRequest, CGR:N/A, USR:elastic (attempted), BRS:true, KDX:null, ACT:cluster:monitor/main, OA:172.29.0.6/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/, CNT:<N/A>, HDR:Accept-Encoding=gzip, Accept=application/json, Authorization=<OMITTED>, Host=elasticsearch:9200, User-Agent=Go-http-client/1.1, content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:25:04,420Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:957643791-1078736626#3169321, TYP:MainRequest, CGR:N/A, USR:elastic (attempted), BRS:true, KDX:null, ACT:cluster:monitor/main, OA:172.29.0.6/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/, CNT:<N/A>, HDR:Accept-Encoding=gzip, Accept=application/json, Authorization=<OMITTED>, Host=elasticsearch:9200, User-Agent=Go-http-client/1.1, content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:25:34,423Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:1719696278-1200022381#3170273, TYP:MainRequest, CGR:N/A, USR:elastic (attempted), BRS:true, KDX:null, ACT:cluster:monitor/main, OA:172.29.0.6/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/, CNT:<N/A>, HDR:Accept-Encoding=gzip, Accept=application/json, Authorization=<OMITTED>, Host=elasticsearch:9200, User-Agent=Go-http-client/1.1, content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:25:58,987Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:560041375-2145265539#3171011, TYP:RRUserMetadataRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:cluster:ror/user_metadata/get, OA:172.29.0.3/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/_readonlyrest/metadata/current_user, CNT:<N/A>, HDR:Accept-Encoding=gzip,deflate, Accept=*/*, Connection=close, Host=elasticsearch:9200, User-Agent=node-fetch/1.0 (+https://github.com/bitinn/node-fetch), content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:26:04,431Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:140620292-862692135#3171454, TYP:MainRequest, CGR:N/A, USR:elastic (attempted), BRS:true, KDX:null, ACT:cluster:monitor/main, OA:172.29.0.6/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/, CNT:<N/A>, HDR:Accept-Encoding=gzip, Accept=application/json, Authorization=<OMITTED>, Host=elasticsearch:9200, User-Agent=Go-http-client/1.1, content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:26:05,293Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:1768447839-691677021#3171463, TYP:RRUserMetadataRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:cluster:ror/user_metadata/get, OA:172.29.0.3/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/_readonlyrest/metadata/current_user, CNT:<N/A>, HDR:Accept-Encoding=gzip,deflate, Accept=*/*, Connection=close, Host=elasticsearch:9200, User-Agent=node-fetch/1.0 (+https://github.com/bitinn/node-fetch), content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:26:34,435Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:651842707-162546661#3172427, TYP:MainRequest, CGR:N/A, USR:elastic (attempted), BRS:true, KDX:null, ACT:cluster:monitor/main, OA:172.29.0.6/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/, CNT:<N/A>, HDR:Accept-Encoding=gzip, Accept=application/json, Authorization=<OMITTED>, Host=elasticsearch:9200, User-Agent=Go-http-client/1.1, content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:27:04,438Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:562804315-1541145977#3173336, TYP:MainRequest, CGR:N/A, USR:elastic (attempted), BRS:true, KDX:null, ACT:cluster:monitor/main, OA:172.29.0.6/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/, CNT:<N/A>, HDR:Accept-Encoding=gzip, Accept=application/json, Authorization=<OMITTED>, Host=elasticsearch:9200, User-Agent=Go-http-client/1.1, content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
elasticsearch_1 | {"type": "server", "timestamp": "2021-12-03T10:27:23,094Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "docker-cluster", "node.name": "404a4d9afc8c", "message": "\u001B[35mFORBIDDEN by default req={ ID:1614342963-1375356540#3174472, TYP:RRUserMetadataRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:cluster:ror/user_metadata/get, OA:172.29.0.3/32, XFF:null, DA:172.29.0.2/32, IDX:<N/A>, MET:GET, PTH:/_readonlyrest/metadata/current_user, CNT:<N/A>, HDR:Accept-Encoding=gzip,deflate, Accept=*/*, Connection=close, Host=elasticsearch:9200, User-Agent=node-fetch/1.0 (+https://github.com/bitinn/node-fetch), content-length=0, HIS:[::LOGSTASH::-> RULES:[auth_key->false]], [::APM::-> RULES:[auth_key->false]], [::KIBANA-SRV::-> RULES:[auth_key->false]], [::ADMIN::-> RULES:[auth_key->false]], [::HEARTBEAT::-> RULES:[auth_key->false]], [::FILEBEAT::-> RULES:[auth_key->false]], [::IGESP::-> RULES:[auth_key->false]], [::GESTAO::-> RULES:[auth_key->false]], [::FRONTEND::-> RULES:[auth_key->false]], [::LDAP_ADMIN::-> RULES:[ldap_auth->false]], [::LDAP_IGESP::-> RULES:[ldap_auth->false]], [::LDAP_GESTAO::-> RULES:[ldap_auth->false]], [::LDAP_FRONTEND::-> RULES:[ldap_auth->false]], }\u001B[0m", "cluster.uuid": "5awwQkafQOeD60FNybj6Mw", "node.id": "lFBD-fWpQCOK9Fr2P2v8mA" }
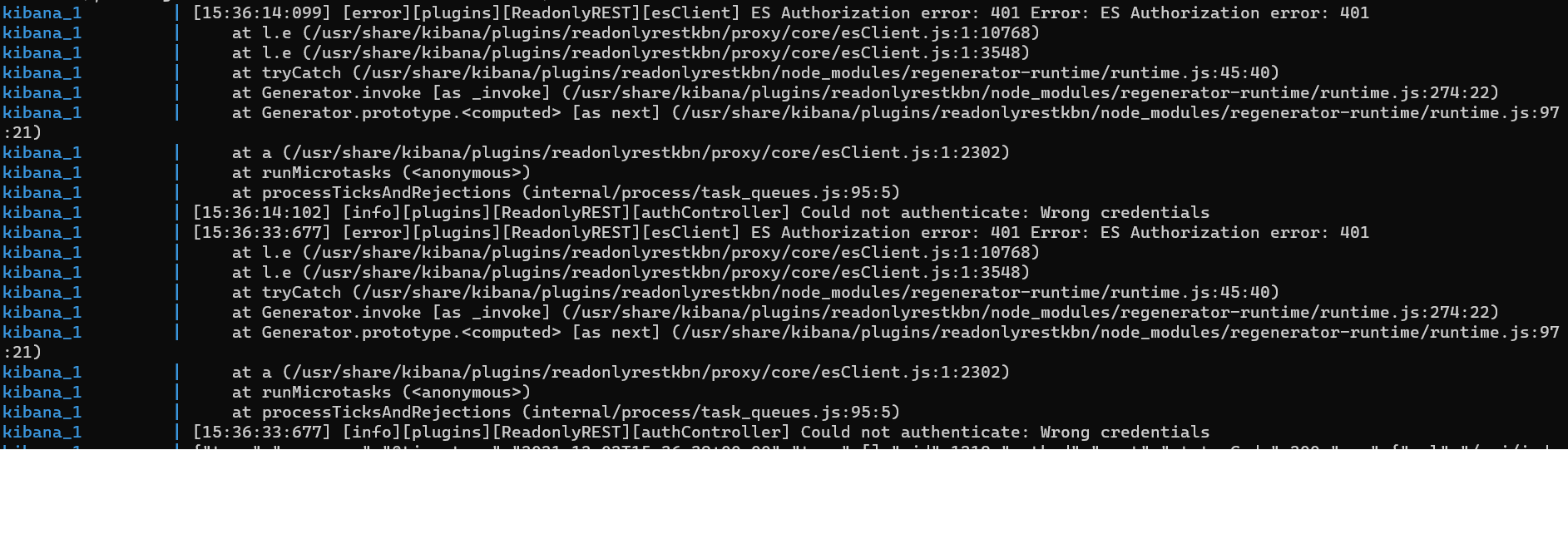

 )
)