Here is couple of log entries with ip/host/port/userid redacted so it loses some of its “value”.
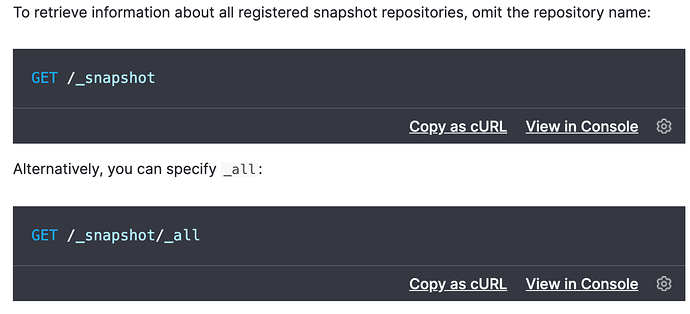
[2020-11-19T13:11:19,466][DEBUG][t.b.r.a.b.Block ] []^[[33m[Audit consumer] the request matches no rules in this block: { ID:1354758091-4610850#133421, TYP:GetRepositoriesRequest, CGR:N/A, USR: (attempted), BRS:true, KDX:null, ACT:cluster:admin/repository/get, OA:/32, XFF:null, DA:/32, IDX:<N/A>, MET:GET, PTH:/_snapshot, CNT:<N/A>, HDR:Accept-Encoding=identity, Authorization=, Connection=close, Host=:, User-Agent=ansible-httpget, content-length=0, HIS:[Audit consumer-> RULES:[ldap_auth->false], RESOLVED:[repositories=_all]] } ^[[0m
[2020-11-19T13:11:19,466][INFO ][t.b.r.a.l.AccessControlLoggingDecorator] []^[[35mFORBIDDEN by default req={ ID:1354758091-4610850#133421, TYP:GetRepositoriesRequest, CGR:N/A, USR: (attempted), BRS:true, KDX:null, ACT:cluster:admin/repository/get, OA:/32, XFF:null, DA:/32, IDX:<N/A>, MET:GET, PTH:/_snapshot, CNT:<N/A>, HDR:Accept-Encoding=identity, Authorization=, Connection=close, Host=:, User-Agent=ansible-httpget, content-length=0, HIS:[DataDog-> RULES:[groups->false], RESOLVED:[repositories=_all]], [cao_etm-> RULES:[ldap_auth->false], RESOLVED:[repositories=_all]], [cognet_consumer-> RULES:[ldap_auth->false], RESOLVED:[repositories=_all]], [cognet_restore_prod_only-> RULES:[ldap_auth->false], RESOLVED:[repositories=_all]], [CEDP_Support-> RULES:[ldap_auth->false], RESOLVED:[repositories=_all]], [CEDP_Admin-> RULES:[ldap_auth->false], RESOLVED:[repositories=_all]], [ICI Producer-> RULES:[ldap_auth->false], RESOLVED:[repositories=_all]], [ICI Consumer-> RULES:[ldap_auth->false], RESOLVED:[repositories=_all]], [Core Ingest-> RULES:[ldap_auth->false], RESOLVED:[repositories=_all]], [Core readers-> RULES:[ldap_auth->false], RESOLVED:[repositories=_all]], [Test producer-> RULES:[ldap_auth->true, repositories->true, actions->false], RESOLVED:[user=;group=es_producer;av_groups=es_producer;repositories=infratest]], [Test consumer-> RULES:[ldap_auth->false], RESOLVED:[repositories=_all]], [Audit producer-> RULES:[ldap_auth->true, actions->false], RESOLVED:[user=;group=es_producer;av_groups=es_producer;repositories=_all]], [Audit consumer-> RULES:[ldap_auth->false], RESOLVED:[repositories=_all]] }^[[0m
Function should match on this block, as the request specifically provide repository name so problem seems to be ROR thinking repository is _all, when in fact it should be for repository “infratest” only:
[Test producer-> RULES:[ldap_auth->true, repositories->true, actions->false], RESOLVED:[user=;group=es_producer;av_groups=es_producer;repositories=infratest]]