I don’t have all the necessary context to answer your question.
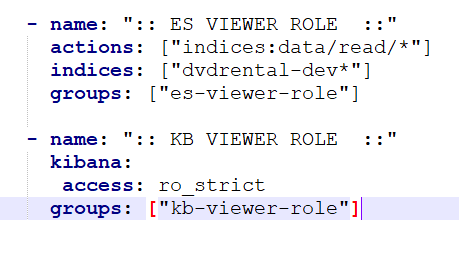
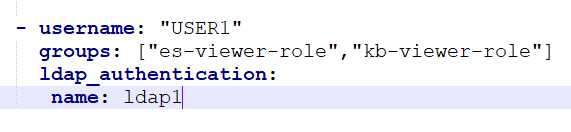
But in the second block, I see a potential misconfiguration in the actions rule. Shouldn’t it be indices:* there?
Block by default has verbosity: info configured which means that for each handled request you should find in logs an “ALLOWED” (when some block was matched) or “FORBIDDEN” (when none block was matched) log.
It looks like this:
[INFO ][t.b.r.a.l.AccessControlLoggingDecorator] [es-ror-single] ALLOWED by { name: 'rwgroup 0', policy: ALLOW, rules: [auth_key,actions,indices] req={ ID:316963062-849947420#2427, TYP:PutComposableIndexTemplateAction$Request, CGR:<N/A>, USR:diana, BRS:true, KDX:null, ACT:indices:admin/index_template/put, OA:172.20.0.3/32, XFF:localhost:15601, DA:172.20.0.2/32, IDX:diana2*, MET:PUT, PTH:/_index_template/diana_test_index_template, CNT:<OMITTED, LENGTH=47.0 B> , HDR:Accept-Charset=utf-8, Authorization=<OMITTED>, Host=es-ror:9200, accept=application/vnd.elasticsearch+json; compatible-with=8, connection=close, content-length=47, content-type=application/vnd.elasticsearch+json; compatible-with=8, cookie=xxx tracestate=es=s:0, user-agent=Kibana/8.6.2, x-elastic-client-meta=es=8.4.0p,js=16.18.1,t=8.2.0,hc=16.18.1, x-elastic-product-origin=kibana, x-forwarded-for=localhost:15601, x-opaque-id=unknownId, x-ror-correlation-id=a83f6ba4-8294-485b-8602-5f0c6d09c4f0, x-ror-kibana-request-method=post, x-ror-kibana-request-path=/s/default/api/index_management/index_templates, HIS:[KIBANA-> RULES:[auth_key->false] RESOLVED:[indices=diana2*;template=ADD(diana_test_index_template:diana2*:)]], [ADMIN-> RULES:[auth_key->false] RESOLVED:[indices=diana2*;template=ADD(diana_test_index_template:diana2*:)]], [rwgroup Kibana-> RULES:[auth_key->true, kibana_access->false] RESOLVED:[user=diana;indices=diana2*;template=ADD(diana_test_index_template:diana2*:)]], [rwgroup 0-> RULES:[auth_key->true, actions->true, indices->true] RESOLVED:[user=diana;indices=diana2*;template=ADD(diana_test_index_template:diana2*:)]], }
This kind of log + ACL configuration are the necessary data to answer what happened. E.g. in the log above you will find:
[rwgroup 0-> RULES:[auth_key->true, actions->true, indices->true]
It means “rwgroup 0” was matched because all the rules in the block were matched.
But in the same log you will find also sth like this:
rwgroup Kibana-> RULES:[auth_key->true, kibana_access->false]
It means that “rwgroup Kibana” was not matched because the kibana_access rule failed to match (even the auth_key rule was matched).
When you check your logs according to the example shown above, you should be able to answer the question