Hello…
I have purchased ReadOnlyRest Pro and I’m just implementing/testing the security and validating the ACLs I’m configuring are working; however, there is one issue I can’t seem to get past.
In the RoR documentation on GitHub https://github.com/sscarduzio/elasticsearch-readonlyrest-plugin#user-content-disallow-explicit-indices - it specifies that ElasticSearch must be configured with the ‘multi.allow_explicit_index’ set to false.
However… Kibana does not support Elasticsearch with this option set: https://github.com/elastic/kibana/pull/10855
Is the documentation still correct, or is there another way we can implement this?
Possible issue related to this setting
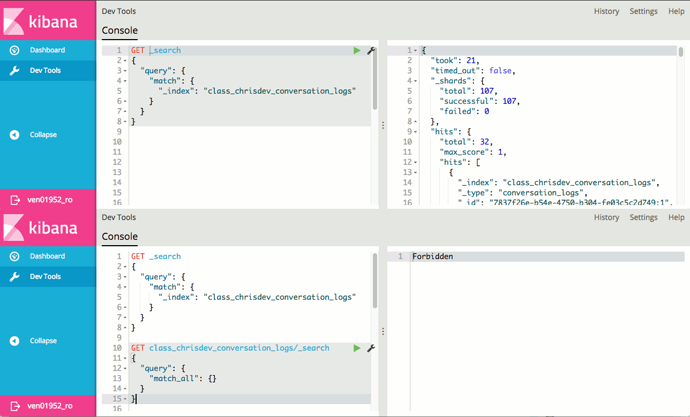
I’m not 100% sure this is related, but if I issue a query from Kibana Dev tools without an explicit index, I definitely do get records back that the user should have no access to. For example:
Above I just run a search on all indices, filtering by an index that that user shouldn’t be able to see, but as shown, all records do come back for that index. The next screenshot (*note: I had to merge the images into one because I couldn’t post 2) shows what happens when I query the index directly (i.e. it gets blocked by RoR as I would expect).
Note that there is an error in the Elasticsearch logs for the first query, so maybe these are actually two separate issues… apologies if that is the case.
The truncated stacktrace from the first query is:
[2017-07-06T04:05:46,901][ERROR][o.e.p.r.e.a.ACLActionListener] indices_rewrite error handling response:
java.util.NoSuchElementException
at java.util.HashMap$HashIterator.nextNode(HashMap.java:1439)
at java.util.HashMap$KeyIterator.next(HashMap.java:1461)
at org.elasticsearch.plugin.readonlyrest.es.actionlisteners.IndicesRewriteSyncRuleActionListener.handleSearchResponse(IndicesRewriteSyncRuleActionListener.java:122)
at org.elasticsearch.plugin.readonlyrest.es.actionlisteners.IndicesRewriteSyncRuleActionListener.onResponse(IndicesRewriteSyncRuleActionListener.java:62)
at org.elasticsearch.plugin.readonlyrest.es.actionlisteners.IndicesRewriteSyncRuleActionListener.onResponse(IndicesRewriteSyncRuleActionListener.java:45)
at org.elasticsearch.plugin.readonlyrest.es.actionlisteners.RuleActionListener.onResponse(RuleActionListener.java:46)
at org.elasticsearch.plugin.readonlyrest.es.actionlisteners.ACLActionListener.lambda$onResponse$0(ACLActionListener.java:61)
at java.util.Optional.map(Optional.java:215)
at org.elasticsearch.plugin.readonlyrest.es.actionlisteners.ACLActionListener.onResponse(ACLActionListener.java:61)
...
Since this is my first query, I wasn’t sure whether the preferred option was to post on the forum or raise an issue on Github. I’m happy to raise an issue on GitHub if that is required (and I can work out whether it is actually an issue or not).
Thanks for you time…