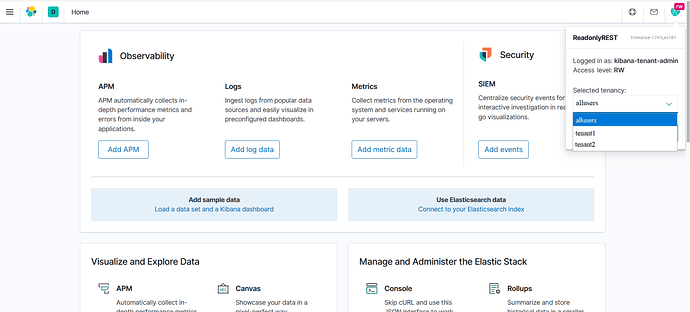
My company is a ReadonlyREST Enterprise subscriber.
I am using LDAP to authenticate customers to my ELK cluster.
The users belong in a specific tenant LDAP group.
I also have a tenant admin LDAP user called “kibana-tenant-admin” who is part of ALL the tenant LDAP groups.
Requirements:
- All customer users in the LDAP groups tenant1 and tenant2 to not be able to see and access the “Stack Management” section in Kibana.
- The “kibana-tenant-admin” user who is part of the LDAP groups tenant1 and tenant2 should be able to switch to these groups → Access the “Stack Management” section in Kibana → Create index patterns and other Kibana objects for these tenants.
By doing this users from tenant1 will only see Kibana objects (like index patterns, dashboards, etc.) created for tenant1 and users from tenant2 will only see Kibana objects (like index patterns, dashboards, etc.) created for tenant2.
Why am I using an LDAP admin user for this ?
Because from what I see a local admin user is not able to switch between the tenant LDAP groups and create Kibana objects (like index patterns, dashboards, etc.) in their .kibana* indices.
The code that I have so far:
- name: "Kibana Tenant Admin" ldap_auth: name: "ldap1" users: ["kibana-tenant-admin"] groups: ["allusers","tenant1","tenant2"] indices: [".kibana*","tenant1*","tenant2*"] kibana_access: rw kibana_index: ".kibana_tenants" - name: "tenant1 Indices" ldap_auth: name: "ldap1" groups: ["tenant1"] indices: [".kibana*","tenant1*"] kibana_access: rw kibana_index: ".kibana_tenant1" kibana_hide_apps: ["readonlyrest_kbn", "timelion", "ml", "infra:home", "apm", "uptime", "siem", "monitoring", "kibana:management","kibana:stack_management"] - name: "tenant2 Indices" ldap_auth: name: "ldap1" groups: ["tenant2"] indices: [".kibana*","tenant2*"] kibana_access: rw kibana_index: ".kibana_tenant2" kibana_hide_apps: ["readonlyrest_kbn", "timelion", "ml", "infra:home", "apm", "uptime", "siem", "monitoring", "kibana:management","kibana:stack_management"]
This code seems to give customer users in tenant1 and tenant2 LDAP groups access to the “Stack Management” section of Kibana, which is what I don’t want.