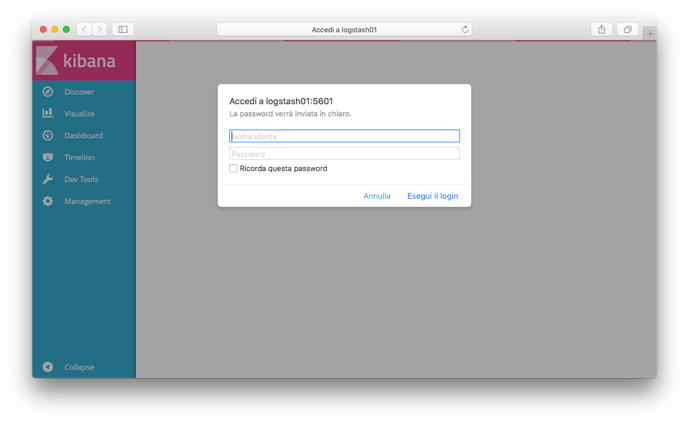
Hi @sscarduzio and @ksondere, I have similar issue.
I’m trying ROR basic in order to have multiple Kibana users. I’ve copied/pasted some configuration examples.
I’m playing with a single server test environment (collapsed ELK stack).
When I access Kibana from browser, I’m asked “just” twice for user credential
My ROR config is:
readonlyrest:
ssl:
enable: true
keystore_file: "/etc/elasticsearch/keystore.jks"
keystore_pass: readonlyrest
key_pass: readonlyrest
response_if_req_forbidden: Forbidden by ReadonlyREST ES plugin
access_control_rules:
- name: "::LOGSTASH::"
auth_key: logstash:logstash
actions: ["cluster:monitor/main","indices:admin/types/exists","indices:data/read/*","indices:data/write/*","indices:admin/template/*","indices:admin/create"]
indices: ["logstash-*"]
- name: "::KIBANA-SRV::"
# auth_key is good for testing, but replace it with `auth_key_sha256`!
auth_key: kibana:kibana
verbosity: error # don't log successful request
- name: "::RW DEVELOPER::"
auth_key: rw:dev
kibana_access: rw
indices: [".kibana", ".kibana-devnull", "shakespeare"]
- name: "::RO DEVELOPER::"
auth_key: ro:dev
kibana_access: ro
indices: [".kibana", ".kibana-devnull", "shakespeare"]
Kibana is configured with ::KIBANA SRV:: credential:
elasticsearch.username: "kibana"
elasticsearch.password: "kibana"
When I access Kibana from browser I’m asked twice for user credential.
These areElasticsearch logs for the first login request:
[2017-10-13T12:15:28,718][INFO ][o.e.p.r.a.ACL ] FORBIDDEN by default req={ ID:1740919866-127920579#9971, TYP:GetRequest, CGR:N/A, USR:[no basic auth header], BRS:false, ACT:indices:data/read/get, OA:127.0.0.1, IDX:.kibana, MET:GET, PTH:/.kibana/config/5.5.1, CNT:<N/A>, HDR:Connection,Content-Length,Host, HIS:[::RW DEVELOPER::->[auth_key->false]], [::KIBANA-SRV::->[auth_key->false]], [::RO DEVELOPER::->[auth_key->false]], [::LOGSTASH::->[auth_key->false]] }
[2017-10-13T12:15:28,857][INFO ][o.e.p.r.a.ACL ] FORBIDDEN by default req={ ID:469270478-1372077889#9984, TYP:GetRequest, CGR:N/A, USR:[no basic auth header], BRS:false, ACT:indices:data/read/get, OA:127.0.0.1, IDX:.kibana, MET:GET, PTH:/.kibana/config/5.5.1, CNT:<N/A>, HDR:Connection,Content-Length,Host, HIS:[::KIBANA-SRV::->[auth_key->false]], [::RO DEVELOPER::->[auth_key->false]], [::LOGSTASH::->[auth_key->false]], [::RW DEVELOPER::->[auth_key->false]] }
After first successful login, I’m requested for second authentication:
Elasticsearch logs:
[2017-10-13T12:21:39,922][INFO ][o.e.p.r.a.ACL ] ALLOWED by '{ block=::RO DEVELOPER::, match=true }' req={ ID:195942657-1078251637#11808, TYP:GetRequest, CGR:N/A, USR:ro, BRS:false, ACT:indices:data/read/get, OA:127.0.0.1, IDX:.kibana, MET:GET, PTH:/.kibana/config/5.5.1, CNT:<N/A>, HDR:authorization,Connection,Content-Length,Host, HIS:[::LOGSTASH::->[auth_key->false]], [::RW DEVELOPER::->[auth_key->false]], [::RO DEVELOPER::->[kibana_access->true, indices->true, auth_key->true]], [::KIBANA-SRV::->[auth_key->false]] }
[2017-10-13T12:21:41,245][INFO ][o.e.p.r.a.ACL ] FORBIDDEN by default req={ ID:625695617-1301760087#11810, TYP:SearchRequest, CGR:N/A, USR:[no basic auth header], BRS:false, ACT:indices:data/read/search, OA:127.0.0.1, IDX:.kibana, MET:POST, PTH:/.kibana/index-pattern/_search?stored_fields=, CNT:<OMITTED, LENGTH=39>, HDR:Connection,content-length,content-type,Host,x-forwarded-for,x-forwarded-port,x-forwarded-proto, HIS:[::LOGSTASH::->[auth_key->false]], [::RW DEVELOPER::->[auth_key->false]], [::RO DEVELOPER::->[auth_key->false]], [::KIBANA-SRV::->[auth_key->false]] }
And after second successful login:
[2017-10-13T12:21:45,361][INFO ][o.e.p.r.a.ACL ] ALLOWED by '{ block=::RO DEVELOPER::, match=true }' req={ ID:746718058-1301760087#11835, TYP:SearchRequest, CGR:N/A, USR:ro, BRS:false, ACT:indices:data/read/search, OA:127.0.0.1, IDX:.kibana, MET:POST, PTH:/.kibana/index-pattern/_search?stored_fields=, CNT:<OMITTED, LENGTH=39>, HDR:authorization,Connection,content-length,content-type,Host,x-forwarded-for,x-forwarded-port,x-forwarded-proto, HIS:[::LOGSTASH::->[auth_key->false]], [::KIBANA-SRV::->[auth_key->false]], [::RW DEVELOPER::->[auth_key->false]], [::RO DEVELOPER::->[kibana_access->true, indices->true, auth_key->true]] }
[2017-10-13T12:21:45,404][INFO ][o.e.p.r.a.ACL ] FORBIDDEN by default req={ ID:715144801-960126676#11837, TYP:GetFieldMappingsRequest, CGR:N/A, USR:[no basic auth header], BRS:false, ACT:indices:admin/mappings/fields/get, OA:127.0.0.1, IDX:.kibana, MET:GET, PTH:/.kibana/_mapping/*/field/_source, CNT:<N/A>, HDR:Connection,content-length,Host,x-forwarded-for,x-forwarded-port,x-forwarded-proto, HIS:[::KIBANA-SRV::->[auth_key->false]], [::LOGSTASH::->[auth_key->false]], [::RW DEVELOPER::->[auth_key->false]], [::RO DEVELOPER::->[auth_key->false]] }
[2017-10-13T12:21:45,421][INFO ][o.e.p.r.a.ACL ] ALLOWED by '{ block=::RO DEVELOPER::, match=true }' req={ ID:49897651-107129350#11838, TYP:GetFieldMappingsRequest, CGR:N/A, USR:ro, BRS:false, ACT:indices:admin/mappings/fields/get, OA:127.0.0.1, IDX:.kibana, MET:GET, PTH:/.kibana/_mapping/*/field/_source, CNT:<N/A>, HDR:authorization,Connection,content-length,Host,x-forwarded-for,x-forwarded-port,x-forwarded-proto, HIS:[::RO DEVELOPER::->[kibana_access->true, indices->true, auth_key->true]], [::LOGSTASH::->[auth_key->false]], [::KIBANA-SRV::->[auth_key->false]], [::RW DEVELOPER::->[auth_key->false]] }
[2017-10-13T12:21:45,421][INFO ][o.e.p.r.a.ACL ] ALLOWED by '{ block=::RO DEVELOPER::, match=true }' req={ ID:49897651-1248114176#11839, TYP:GetFieldMappingsIndexRequest, CGR:N/A, USR:ro, BRS:false, ACT:indices:admin/mappings/fields/get[index], OA:127.0.0.1, IDX:.kibana, MET:GET, PTH:/.kibana/_mapping/*/field/_source, CNT:<N/A>, HDR:authorization,Connection,content-length,Host,x-forwarded-for,x-forwarded-port,x-forwarded-proto, HIS:[::RO DEVELOPER::->[kibana_access->true, indices->true, auth_key->true]], [::KIBANA-SRV::->[auth_key->false]], [::LOGSTASH::->[auth_key->false]], [::RW DEVELOPER::->[auth_key->false]] }
[2017-10-13T12:21:45,460][INFO ][o.e.p.r.a.ACL ] FORBIDDEN by default req={ ID:1957507666-2022268324#11841, TYP:MultiGetRequest, CGR:N/A, USR:[no basic auth header], BRS:false, ACT:indices:data/read/mget, OA:127.0.0.1, IDX:.kibana, MET:POST, PTH:/_mget, CNT:<OMITTED, LENGTH=75>, HDR:Connection,content-length,content-type,Host,x-forwarded-for,x-forwarded-port,x-forwarded-proto, HIS:[::RW DEVELOPER::->[auth_key->false]], [::LOGSTASH::->[auth_key->false]], [::KIBANA-SRV::->[auth_key->false]], [::RO DEVELOPER::->[auth_key->false]] }
[2017-10-13T12:21:45,478][INFO ][o.e.p.r.a.ACL ] ALLOWED by '{ block=::RO DEVELOPER::, match=true }' req={ ID:157960993-1578005720#11842, TYP:MultiGetRequest, CGR:N/A, USR:ro, BRS:false, ACT:indices:data/read/mget, OA:127.0.0.1, IDX:.kibana, MET:POST, PTH:/_mget, CNT:<OMITTED, LENGTH=75>, HDR:authorization,Connection,content-length,content-type,Host,x-forwarded-for,x-forwarded-port,x-forwarded-proto, HIS:[::LOGSTASH::->[auth_key->false]], [::RO DEVELOPER::->[kibana_access->true, indices->true, auth_key->true]], [::KIBANA-SRV::->[auth_key->false]], [::RW DEVELOPER::->[auth_key->false]] }
[2017-10-13T12:21:45,479][INFO ][o.e.p.r.a.ACL ] ALLOWED by '{ block=::RO DEVELOPER::, match=true }' req={ ID:157960993-1200412825#11843, TYP:MultiGetShardRequest, CGR:N/A, USR:ro, BRS:false, ACT:indices:data/read/mget[shard], OA:127.0.0.1, IDX:.kibana, MET:POST, PTH:/_mget, CNT:<OMITTED, LENGTH=75>, HDR:authorization,Connection,content-length,content-type,Host,x-forwarded-for,x-forwarded-port,x-forwarded-proto, HIS:[::KIBANA-SRV::->[auth_key->false]], [::RW DEVELOPER::->[auth_key->false]], [::LOGSTASH::->[auth_key->false]], [::RO DEVELOPER::->[kibana_access->true, indices->true, auth_key->true]] }
[2017-10-13T12:21:45,998][INFO ][o.e.p.r.a.ACL ] FORBIDDEN by default req={ ID:424412532-807539838#11845, TYP:MultiSearchRequest, CGR:N/A, USR:[no basic auth header], BRS:false, ACT:indices:data/read/msearch, OA:127.0.0.1, IDX:shakespeare, MET:POST, PTH:/_msearch, CNT:<OMITTED, LENGTH=436>, HDR:Connection,content-length,content-type,Host,x-forwarded-for,x-forwarded-port,x-forwarded-proto, HIS:[::RO DEVELOPER::->[auth_key->false]], [::LOGSTASH::->[auth_key->false]], [::KIBANA-SRV::->[auth_key->false]], [::RW DEVELOPER::->[auth_key->false]] }
[2017-10-13T12:21:46,013][INFO ][o.e.p.r.a.ACL ] ALLOWED by '{ block=::RO DEVELOPER::, match=true }' req={ ID:728480146-250604187#11846, TYP:MultiSearchRequest, CGR:N/A, USR:ro, BRS:false, ACT:indices:data/read/msearch, OA:127.0.0.1, IDX:shakespeare, MET:POST, PTH:/_msearch, CNT:<OMITTED, LENGTH=436>, HDR:authorization,Connection,content-length,content-type,Host,x-forwarded-for,x-forwarded-port,x-forwarded-proto, HIS:[::RW DEVELOPER::->[auth_key->false]], [::LOGSTASH::->[auth_key->false]], [::KIBANA-SRV::->[auth_key->false]], [::RO DEVELOPER::->[kibana_access->true, indices->true, auth_key->true]] }
[2017-10-13T12:21:46,014][INFO ][o.e.p.r.a.ACL ] ALLOWED by '{ block=::RO DEVELOPER::, match=true }' req={ ID:728480146-1864178784#11847, TYP:SearchRequest, CGR:N/A, USR:ro, BRS:false, ACT:indices:data/read/search, OA:127.0.0.1, IDX:shakespeare, MET:POST, PTH:/_msearch, CNT:<OMITTED, LENGTH=436>, HDR:authorization,Connection,content-length,content-type,Host,x-forwarded-for,x-forwarded-port,x-forwarded-proto, HIS:[::KIBANA-SRV::->[auth_key->false]], [::RW DEVELOPER::->[auth_key->false]], [::LOGSTASH::->[auth_key->false]], [::RO DEVELOPER::->[kibana_access->true, indices->true, auth_key->true]] }
Can you tell me what is wrong?