Hi.
I am testing the SAML integration of the Enterprise version of Kibana Plugin. My current setup is:
- Elasticsearch 7.16.1
- Kibaba 7.16.1
- Elasticsearch ROR plugin readonlyrest-1.39.0_es7.17.3.zip
- Kibana ROR plugin readonlyrest_kbn_enterprise-1.43.0-20220902_es7.16.1.zip
- keycloak 19.0.2
The content of kibana.yaml:
readonlyrest_kbn.auth:
signature_key: "long key"
saml_serv1:
enabled: true
type: saml
issuer: ror
buttonName: "Partner's SSO Login"
entryPoint: 'http://localhost:8081/realms/LDAP/broker/saml/endpoint'
kibanaExternalHost: 'vkibana.obs'
protocol: https
usernameParameter: 'nameID'
groupsParameter: 'memberOf'
logoutUrl: 'idp logout url'
cert: 'path/to/idp/certificate'
And the contet of readonlyrest.yaml:
readonlyrest:
audit_collector: true
audit_index_template: "'readonlyrest_audit'-yyyy"
prompt_for_basic_auth: true
ssl:
enable: true
keystore_file: keystore.jks
keystore_pass: changeme
key_pass: changeme
response_if_req_forbidden: Access forbidden
access_control_rules:
- name: "::KIBANA-SRV::"
auth_key: kibana:kibana
kibana_access: admin
indices: ["*"]
verbosity: error
- name: "ReadonlyREST Enterprise instance #1"
ror_kbn_auth:
name: "kbn1"
verbosity: error
ror_kbn:
- name: kbn1
signature_key: "long key"
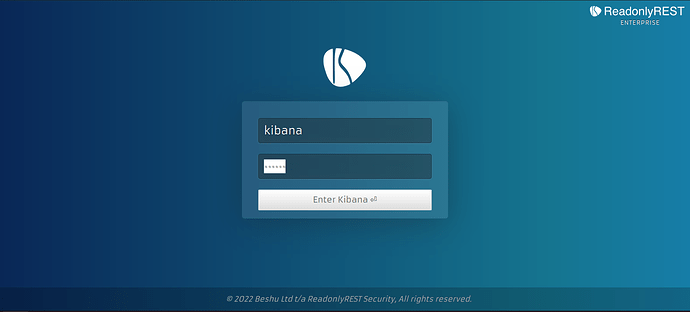
On the browser, this is the login page shown:
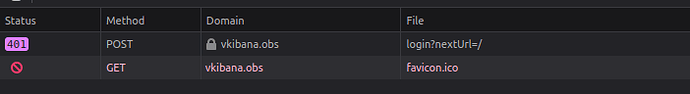
And after submitting valid credentials, this is the result:
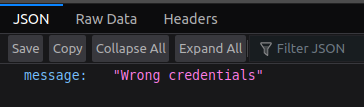
From the browser console, no attempts to reach the IdP are shown:
The logs from elasticsearch:
{"type": "server", "timestamp": "2022-09-22T17:15:38,916Z", "level": "INFO", "component": "t.b.r.c.l.ConfigLoadingInterpreter$", "cluster.name": "piab-cluster", "node.name": "node-piab", "message": "[CLUSTERWIDE SETTINGS] Loading ReadonlyREST settings from index (.readonlyrest) ...", "cluster.uuid": "2FdkiYsAQi2GOfjynLv_rA", "node.id": "Ob8Tn75WTY-V_3vsCK1ipg" }
...
{"type": "server", "timestamp": "2022-09-22T17:15:39,254Z", "level": "WARN", "component": "t.b.r.e.IndexLevelActionFilter", "cluster.name": "piab-cluster", "node.name": "node-piab", "message": "[486554789-2063101315#90] Cannot handle the request /_nodes because ReadonlyREST hasn't started yet", "cluster.uuid": "2FdkiYsAQi2GOfjynLv_rA", "node.id": "Ob8Tn75WTY-V_3vsCK1ipg" }
...
{"type": "server", "timestamp": "2022-09-22T17:16:04,239Z", "level": "INFO", "component": "t.b.r.a.f.RawRorConfigBasedCoreFactory", "cluster.name": "piab-cluster", "node.name": "node-piab", "message": "ADDING BLOCK:\t{ name: 'ReadonlyREST Enterprise instance #1', policy: ALLOW, rules: [ror_kbn_auth]", "cluster.uuid": "2FdkiYsAQi2GOfjynLv_rA", "node.id": "Ob8Tn75WTY-V_3vsCK1ipg" }
{"type": "server", "timestamp": "2022-09-22T17:16:04,254Z", "level": "INFO", "component": "t.b.r.b.RorInstance", "cluster.name": "piab-cluster", "node.name": "node-piab", "message": "ReadonlyREST core was loaded ...", "cluster.uuid": "2FdkiYsAQi2GOfjynLv_rA", "node.id": "Ob8Tn75WTY-V_3vsCK1ipg" }
...
{"type": "server", "timestamp": "2022-09-22T17:38:58,591Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "piab-cluster", "node.name": "node-piab", "message": "\u001B[35mFORBIDDEN by default req={ ID:1376486176-386471685#4693, TYP:RRUserMetadataRequest, CGR:N/A, USR:[no info about user], BRS:true, KDX:null, ACT:cluster:ror/user_metadata/get, OA:10.191.1.59/32, XFF:null, DA:10.191.1.58/32, IDX:<N/A>, MET:GET, PTH:/_readonlyrest/metadata/current_user, CNT:<N/A>, HDR:Accept-Encoding=gzip,deflate, Accept=*/*, Connection=close, Host=velasticsearch:9200, User-Agent=node-fetch/1.0 (+https://github.com/bitinn/node-fetch), content-length=0, HIS:[::KIBANA-SRV::-> RULES:[auth_key->false]], [ReadonlyREST Enterprise instance #1-> RULES:[ror_kbn_auth->false]], }\u001B[0m", "cluster.uuid": "2FdkiYsAQi2GOfjynLv_rA", "node.id": "Ob8Tn75WTY-V_3vsCK1ipg" }
{"type": "server", "timestamp": "2022-09-22T17:38:59,179Z", "level": "INFO", "component": "t.b.r.a.l.AccessControlLoggingDecorator", "cluster.name": "piab-cluster", "node.name": "node-piab", "message": "\u001B[35mFORBIDDEN by default req={ ID:1935410978-209393980#4694, TYP:NodesInfoRequest, CGR:N/A, USR:kibana_system (attempted), BRS:true, KDX:null, ACT:cluster:monitor/nodes/info, OA:10.191.1.59/32, XFF:null, DA:10.191.1.58/32, IDX:<N/A>, MET:GET, PTH:/_nodes, CNT:<N/A>, HDR:Accept-Charset=utf-8, Authorization=<OMITTED>, Host=velasticsearch:9200, connection=close, content-length=0, user-agent=elasticsearch-js/7.16.0-canary.7 (linux 5.14.0-1051-oem-x64; Node.js v16.13.0), x-elastic-client-meta=es=7.16.0p,js=16.13.0,t=7.16.0p,hc=16.13.0, x-elastic-product-origin=kibana, HIS:[::KIBANA-SRV::-> RULES:[auth_key->false]], [ReadonlyREST Enterprise instance #1-> RULES:[ror_kbn_auth->false]], }\u001B[0m", "cluster.uuid": "2FdkiYsAQi2GOfjynLv_rA", "node.id": "Ob8Tn75WTY-V_3vsCK1ipg" }
The current setup works fine with LDAP authentication.
Thanks in advance