Hi.
After configuring SAML integration in Kibana, when trying to authenticate, I have the following error:
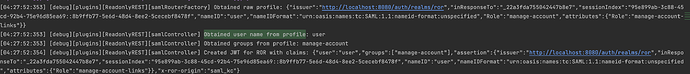
[00:23:30:843] [info][plugins][ReadonlyREST][authController] Could not login in: Empty metadata
This is the kibana configuration related to SAML:
readonlyrest_kbn.auth:
signature_key: "key"
saml_serv1:
enabled: true
type: saml
issuer: https://vkibana.obs
buttonName: "Keycloak"
entryPoint: 'https://vkeycloak.obs/realms/LDAP/protocol/saml'
kibanaExternalHost: 'vkibana.obs'
protocol: https
usernameParameter: 'NameID'
groupsParameter: 'memberOf'
logoutUrl: 'https://vkeycloak.obs/realms/LDAP/protocol/saml/resolve'
cert: 'certificate'
And this is the elasticsearch configuration:
- name: "ReadonlyREST Enterprise instance #1"
ror_kbn_auth:
name: "kbn1"
ror_kbn:
- name: kbn1
signature_key: "key"
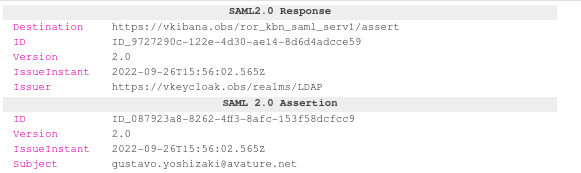
This is a sample of the SAML Response sent by the IdP:
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
Destination="https://vkibana.obs/ror_kbn_saml_serv1/assert"
ID="ID_6a96d1f2-a3c7-41cf-90f7-494ac80e4a36"
InResponseTo="_f9cc74a0c7103dbbb003"
IssueInstant="2022-09-25T00:23:30.656Z"
Version="2.0"
>
<saml:Issuer>https://vkeycloak.obs/realms/LDAP</saml:Issuer>
<dsig:Signature xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:SignedInfo>
<dsig:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
<dsig:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256" />
<dsig:Reference URI="#ID_6a96d1f2-a3c7-41cf-90f7-494ac80e4a36">
<dsig:Transforms>
<dsig:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" />
<dsig:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</dsig:Transforms>
<dsig:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256" />
<dsig:DigestValue>digest</dsig:DigestValue>
</dsig:Reference>
</dsig:SignedInfo>
<dsig:SignatureValue>signature</dsig:SignatureValue>
<dsig:KeyInfo>
<dsig:KeyName>D-Iv4jANhgLQVYAv_a0OhHeEh8EQA0uViZHjGXlbdQA</dsig:KeyName>
<dsig:X509Data>
<dsig:X509Certificate>certificate</dsig:X509Certificate>
</dsig:X509Data>
<dsig:KeyValue>
<dsig:RSAKeyValue>
<dsig:Modulus>key</dsig:Modulus>
<dsig:Exponent>AQAB</dsig:Exponent>
</dsig:RSAKeyValue>
</dsig:KeyValue>
</dsig:KeyInfo>
</dsig:Signature>
<samlp:Status>
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success" />
</samlp:Status>
<saml:Assertion xmlns="urn:oasis:names:tc:SAML:2.0:assertion"
ID="ID_cc5a8457-ac9c-4902-9c3c-69155e98bffe"
IssueInstant="2022-09-25T00:23:30.656Z"
Version="2.0"
>
<saml:Issuer>https://vkeycloak.obs/realms/LDAP</saml:Issuer>
<saml:Subject>
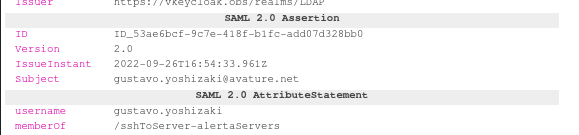
<saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">gustavo.yoshizaki@avature.net</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<saml:SubjectConfirmationData InResponseTo="_f9cc74a0c7103dbbb003"
NotOnOrAfter="2022-09-25T00:28:28.656Z"
Recipient="https://vkibana.obs/ror_kbn_saml_serv1/assert"
/>
</saml:SubjectConfirmation>
</saml:Subject>
<saml:Conditions NotBefore="2022-09-25T00:23:28.656Z"
NotOnOrAfter="2022-09-25T00:24:28.656Z"
>
<saml:AudienceRestriction>
<saml:Audience>https://vkibana.obs</saml:Audience>
</saml:AudienceRestriction>
</saml:Conditions>
<saml:AuthnStatement AuthnInstant="2022-09-25T00:23:30.657Z"
SessionIndex="467f57d8-53d6-493e-9925-55e76764d452::e28803c3-3242-4c36-bb0d-88f0b29afea0"
SessionNotOnOrAfter="2022-09-25T10:23:30.657Z"
>
<saml:AuthnContext>
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:unspecified</saml:AuthnContextClassRef>
</saml:AuthnContext>
</saml:AuthnStatement>
<saml:AttributeStatement>
<saml:Attribute Name="Role"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"
>
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string"
>manage-account-links</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="Role"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"
>
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string"
>uma_authorization</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="Role"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"
>
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string"
>view-profile</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="Role"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"
>
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string"
>manage-account</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="Role"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"
>
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string"
>offline_access</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="Role"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"
>
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string"
>default-roles-ldap</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
</samlp:Response>
I also tried using saml:NameID as usernameParameter without success.
Thanks in advance.